

| Current | v9 | v8 | v7 | v6 | v5 | v4 | v3 | v2 | v1 | All | About |
Part II
Determining that the previous testing methodology is not effective, a re-engineering of the test case has been implemented and re-testing the driver to hit the missed block can now be accomplished. Following the steps provided in Part I, the driver is loaded into the Virtual PC, kd is attached to the driver process, and Debug Stalk has been loaded into kd and has been invoked to run by using the 'g' command. The entire process is the same except that when the new fuzz test is invoked, different output is printed to kd:
kd> g
[*] - Recorder Opened......: pluto.sys.0
[*] - Recorder Opened......: pluto.sys-regs.0
Modload: Processing breakpoints for module pluto.sys at f7a27000
Modload: Done. 46 of 46 breakpoints were set.
004047a0 T:00000001 [bp] f7a2b000 a100a0a2f7 mov eax,dword ptr [pluto+0x3000 (f7a2a000)]
004052bc T:00000001 [bp] f7a2b00e 3bc1 cmp eax,ecx
00405339 T:00000001 [bp] f7a2b012 a12890a2f7 mov eax,dword ptr [pluto+0x2028 (f7a29028)]
004053e5 T:00000001 [bp] f7a2b02b e9aed1ffff jmp pluto+0x11de (f7a281de)
00405462 T:00000001 [bp] f7a281de 55 push ebp
004054ee T:00000001 [bp] f7a28219 8b45fc mov eax,dword ptr [ebp-4]
0040558b T:00000001 [bp] f7a28253 6844646b20 push 206B6444h
00405617 T:00000001 [bp] f7a282a2 b980000000 mov ecx,80h
00405694 T:00000001 [bp] f7a282ab 5f pop edi
00406ccc T:00000001 [bp] f7a2806a 8b4c2408 mov ecx,dword ptr [esp+8]
00406e04 T:00000001 [bp] f7a280f6 833d04a0a2f700 cmp dword ptr [pluto+0x3004 (f7a2a004)],0
00406eb0 T:00000001 [bp] f7a2810c 8b7760 mov esi,dword ptr [edi+60h]
00406f4c T:00000001 [bp] f7a28114 8b4704 mov eax,dword ptr [edi+4]
00406ff8 T:00000001 [bp] f7a28122 6a10 push 10h
00407075 T:00000001 [bp] f7a28133 85c0 test eax,eax
00407102 T:00000001 [bp] f7a28147 ff7604 push dword ptr [esi+4]
004071ae T:00000001 [bp] f7a28169 6a04 push 4
current context:
eax=00000003 ebx=00000000 ecx=8050589d edx=0000006a esi=00000000 edi=f1499052
eip=804e3b25 esp=f3cbe720 ebp=f3cbe768 iopl=0 nv up ei pl zr na pe nc
cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00000246
nt!RtlpBreakWithStatusInstruction:
804e3b25 cc int 3
commands:
[m] module list [0-9] enter recorder modes
[x] stop recording [v] toggle verbosity
[q] quit/close
kd> k
ChildEBP RetAddr
f3c1971c 805328e7 nt!RtlpBreakWithStatusInstruction
f3c19768 805333be nt!KiBugCheckDebugBreak+0x19
f3c19b48 805339ae nt!KeBugCheck2+0x574
f3c19b68 805246fb nt!KeBugCheckEx+0x1b
f3c19bb4 804e1ff1 nt!MmAccessFault+0x6f5
f3c19bb4 804da1ee nt!KiTrap0E+0xcc
*** ERROR: Module load completed but symbols could not be loaded for pluto.sys
f3c19c48 f79f0173 nt!memmove+0x72
WARNING: Stack unwind information not available. Following frames may be wrong.
f3c19c84 8057a510 pluto+0x1173
f3c19d38 804df06b nt!NtWriteFile+0x602
f3c19d38 7c90eb94 nt!KiFastCallEntry+0xf8
0006fec0 7c90e9ff ntdll!KiFastSystemCallRet
0006fec4 7c81100e ntdll!ZwWriteFile+0xc
0006ff24 01001276 kernel32!WriteFile+0xf7
0006ff44 010013a7 betterfuzz_c!main+0xa4
0006ffc0 7c816d4f betterfuzz_c!mainCRTStartup+0x12f
0006fff0 00000000 kernel32!BaseProcessStart+0x23
current context:
eax=00000003 ebx=00000000 ecx=8050589d edx=0000006a esi=00000000 edi=f1499052
eip=804e3b25 esp=f3c19720 ebp=f3c19768 iopl=0 nv up ei pl zr na pe nc
cs=0008 ss=0010 ds=0023 es=0023 fs=0030 gs=0000 efl=00000246
nt!RtlpBreakWithStatusInstruction:
804e3b25 cc int 3
commands:
[m] module list [0-9] enter recorder modes
[x] stop recording [v] toggle verbosity
[q] quit/close
kd> q
[*] - Exiting Stalker
q
C:\Uninformed>
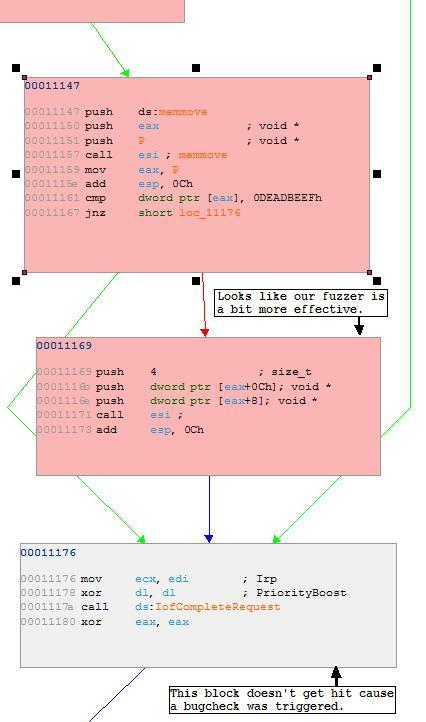
Generating the .gml file allows the tester to view the new execution path. In this case the block at address 00011169 is executed. All subsequent blocks underneath it are not executed because the driver BugChecks inside of this newly hit block indicating a bug of some sort. Command 'k' in kd produces the stack unwind information and we can see that a BugCheck was initiated for an Access Violation that occurs inside of pluto.sys.