| Current | v9 | v8 | v7 | v6 | v5 | v4 | v3 | v2 | v1 | All | About |
Hooking Packets
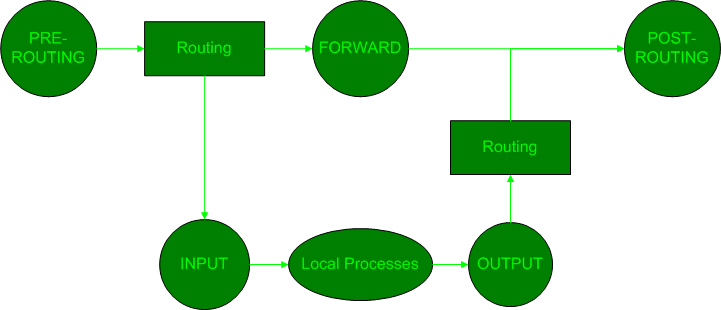
The SteganRTP application makes use of NetFilter[24] hook points in order to receive both inbound and outbound RTP session packets. The Linux kernel is instructed to pass specific packets to an application by inserting an iptables rule describing the packets with a target of QUEUE. Packets which match a rule with a target of QUEUE are queued to be read by a registered NetFilter user-space queuing agent. Access to this queue is provided to the SteganRTP application via an API provided by the NetFilter C library libipq. An iptables rule used to hook packets via this interface may be inserted at any of the NetFilter hook points as indicated by the circle icons in Figure ![[*]](8/3/images/html/crossref.png) below.
below.
For the most beneficial use by the SteganRTP application, packets must be hooked at points where their integrity as stego-medium is maintained. Thus, inbound packets are hooked at the PRE-ROUTING hook point and outbound packets are hooked at the POST-ROUTING hook point. In this manner, incoming packets are able to be processed by the SteganRTP application prior to any potential modification by the local system and outbound packets are able to be modified by SteganRTP after the local system is essentially finished with them.
SteganRTP registers itself as a user-space queuing agent for NetFilter via libipq. SteganRTP then creates two iptables rules in the NetFilter engine with targets of QUEUE. The first rule matches the inbound RTP stream at the PRE-ROUTING hook point. The second rule matches the outbound RTP stream at the POST-ROUTING hook point.