| Current | v9 | v8 | v7 | v6 | v5 | v4 | v3 | v2 | v1 | All | About |
Predictability of Entropy Sources in Boot Start Services
A second attack that could be used against GS involves attacking services that start early on when the system is booted. These services may experience more predictable states of entropy due to the fact that the amount of time it takes to boot up and the order in which tasks are performed is fairly, though not entirely, consistent. This insight may make it possible to estimate the value of entropy sources remotely.
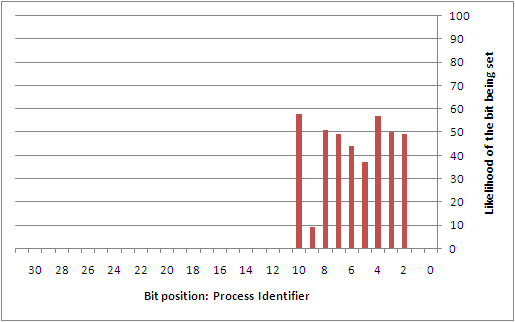
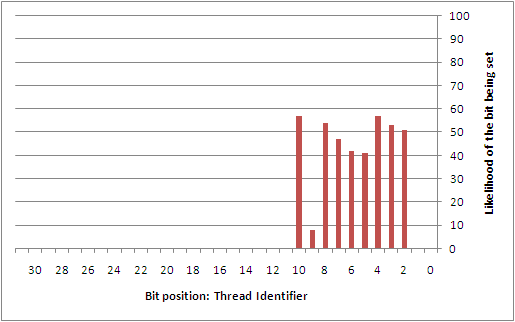
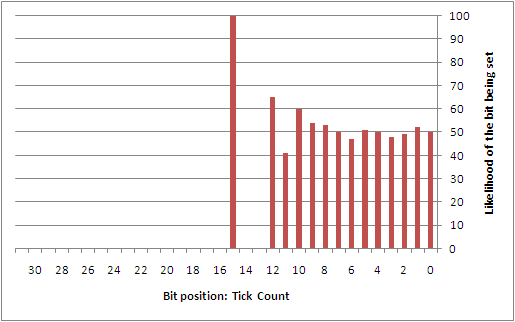
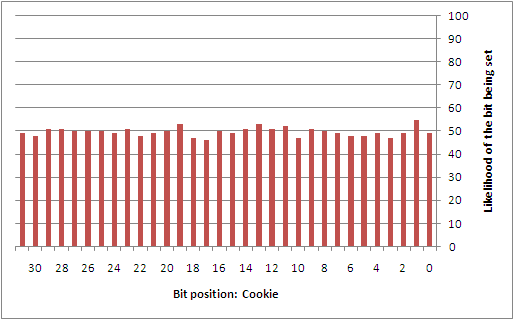
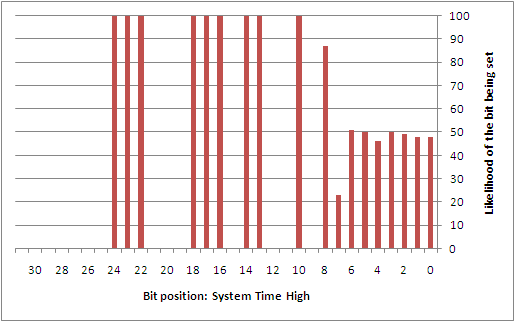
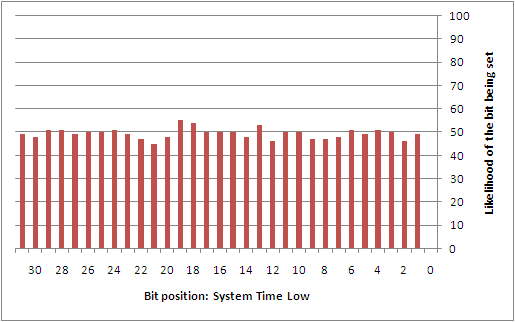
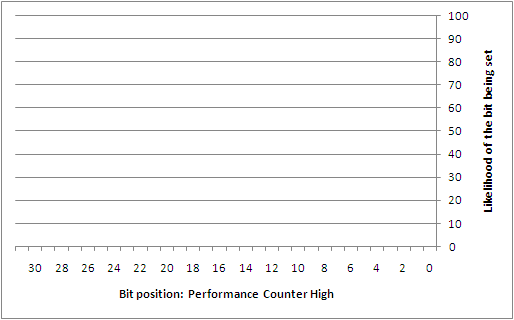
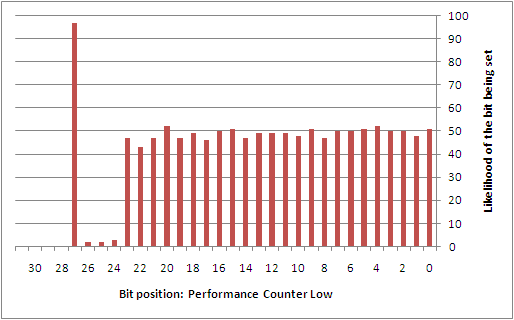
To better understand this type of attack, the author collected 742 samples that were taken from a custom service that was set to automatically start during boot on a Windows XP SP2 installation. This service was simply designed to log the state used at the time that the GS cookie was being generated. While a sampling of the GS cookie state applied to lsass.exe would have been more ideal, it wasn't worth the headache of having to patch a critical system service. Perhaps the reader may find it interesting to collect this data on their own. From the samples that were taken, the following diagrams show the likelihood of each individual bit being set for each of the different entropy sources.
Overall, there are a number of predictable bits in things like the high 32-bits of both the system time and the performance counter, the process identifier, the thread identifier, and the tick count. The sources that are largely unpredictable are the low 32-bits of the system time and the performance counter. However, if it were possible to come up with a way to discover the boot time (or uptime) of the system remotely, it might be possible to infer a good portion of the low 32-bits of the system time. This would then directly impact the ability to estimate things like the tick count and performance counters.
|
|
|
|