| Current | v9 | v8 | v7 | v6 | v5 | v4 | v3 | v2 | v1 | All | About |
What is in a Print Database?
The tools and techniques described in this chapter all operate on a surprisingly little amount of information, stored in what we call a print database. There is a fingerprint for each implementation. A fingerprint comprises a list of records of the form (packet_type, duration-value, count) which reflects the number of times the given duration value appeared for the given packet type. All data and management frames are observed while control packets are discarded.
Two example prints from the same database are given in Tables 4.2 and 4.3. Both prints were generated from packet captures done while a client associates, obtains an IP address from DHCP, and proceeds to load a few web pages. With so little activity, there is a remarkable range of behaviors. These two prints were chosen to illustrate the range of behaviors between Atheros and Prism chipsets.
Table 4.2:
Implementation-Id: 1 (Atheros, ar5211.sys), database: Lexie
![\begin{table}
\begin{center}
\begin{tabular}{\vert l\vert p{3.0in}\vert}
\h...
... & (162 [597/597])\\
\hline
\par
\end{tabular}
\end{center}
\end{table}% WIDTH=489 HEIGHT=119](5/1/img2.png)
Table 4.3:
Implementation-Id: 9 (Prism-2.5, smc2532w.sys), database: Lexie
![\begin{table}
\begin{center}
\begin{tabular}{\vert l\vert p{3.0in}\vert}
\h...
...& (37554 [16/16]) \\
\hline
\par
\end{tabular}
\end{center}
\end{table}% WIDTH=489 HEIGHT=119](5/1/img3.png)
Two things stand out immediately from these fingerprints. The first is that the second implementation (the prism2.5 based implementation) uses duration values that are entirely different than those used by the better behaved Atheros card. Secondly, the prism2.5 based implementation uses two illegal duration values. The standard says that any values greater than 32767 should be ignored.
Though these two implementations are different enough that they can be easily distinguished, most of the other sampled implementations fell somewhere between them. To get better resolution, two ratios were introduced: the ratio of packets with a given duration relative to the total number of packets sampled, and the ratio of pairs (packet type, duration) for a given packet type and duration relative to the total number of packets seen of that packet type.
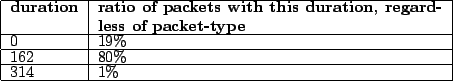
Though these numbers can fluctuate across different samples for the same implementation, they proved to be stable enough to cause an improvement in the algorithms that use them. Tables 4.4 and 4.5 show this information for the Atheros fingerprint above in Table 4.2.
Table 4.4:
Implementation-Id: 1 (Atheros, ar5211.sys), database: Lexie
![\begin{table}
\begin{center}
\begin{tabular}{\vert l\vert p{3.0in}\vert}
\h...
...n & (162 [100\%]) \\
\hline
\par
\end{tabular}
\end{center}
\end{table}% WIDTH=489 HEIGHT=119](5/1/img4.png)
Table 4.5:
Implementation-Id: 1 (Atheros, ar5211.sys), database: Lexie