| Current | v9 | v8 | v7 | v6 | v5 | v4 | v3 | v2 | v1 | All | About |
Calculating Viable Opcode Windows
After analyzing SharedUserData for temporal addresses it
should become clear that the SystemTime attribute is by far
the most useful and potentially feasible attribute due to its scale
and update period. In order to successfully leverage it in
conjunction with an exploit, though, the viable opcode windows must
be calculated so that a time to strike can be selected. This can be
done prior to determining what the actual date is on a target
machine but requires that the storage capacity (size of the temporal
address in bytes), the update period, and the scale be known. In
this case, the size of the SystemTime attribute is 12
bytes, though in reality the 3rd attribute, High2Time, is
exactly the same as the second, High1Time, so all that
really matters are the the first 8 bytes. Doing the math to
calculate per-byte durations gives the results shown in figure
![[*]](images/html/crossref.png) . This indicates that it is only worth focusing on
opcode permutations that start at byte index four due to the fact
that all previous byte indexes have a duration of less than or equal
to one second. By applying the scale as being measured since Jan 1,
1601, all of the possible permutations for the past, present, and
future can be calculated as described in chapter
. This indicates that it is only worth focusing on
opcode permutations that start at byte index four due to the fact
that all previous byte indexes have a duration of less than or equal
to one second. By applying the scale as being measured since Jan 1,
1601, all of the possible permutations for the past, present, and
future can be calculated as described in chapter ![[*]](images/html/crossref.png) .
The results of these calculations for the SystemTime
attribute are described in the following paragraphs.
.
The results of these calculations for the SystemTime
attribute are described in the following paragraphs.
In order to calculate the viable opcode windows it is necessary to
have identified the viable set of opcodes. In this case study a
total of 320 viable opcodes were used (recall that opcode
in this case can mean one or more instruction). These viable
opcodes were taken from the Metasploit Opcode Database[2].
After performing the necessary calculations and generating all of
the permutations, a total of 3615 viable opcode windows
were found between Jan. 1, 1970 and Dec. 23, 2037. Each viable
opcode was broken down into groupings of similar or equivalent
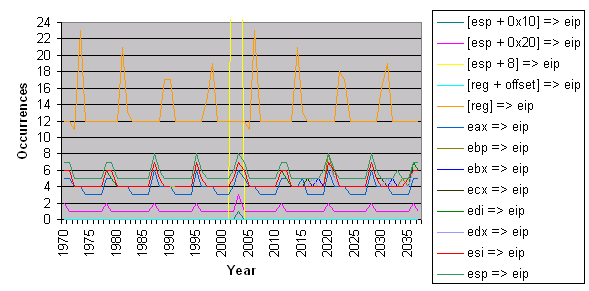
opcodes such that it could be made easier to visualize. Figure
![[*]](images/html/crossref.png) shows a graph of all of the viable opcode windows
between 1970 and 2038 as broken down by opcode groupings.
shows a graph of all of the viable opcode windows
between 1970 and 2038 as broken down by opcode groupings.
Looking closely at figure ![[*]](images/html/crossref.png) it can bee seen that there
were two large spikes around 2002 and 2003 for the [esp + 8]
=> eip opcode group which includes pop/pop/ret
instructions common to SEH overwrites. Looking more closely at these
two years shows that there were two significant periods of time
during 2002 and 2003 where the stars aligned and certain exploits
could have used the SystemTime attribute as a temporal
return address. Figure
it can bee seen that there
were two large spikes around 2002 and 2003 for the [esp + 8]
=> eip opcode group which includes pop/pop/ret
instructions common to SEH overwrites. Looking more closely at these
two years shows that there were two significant periods of time
during 2002 and 2003 where the stars aligned and certain exploits
could have used the SystemTime attribute as a temporal
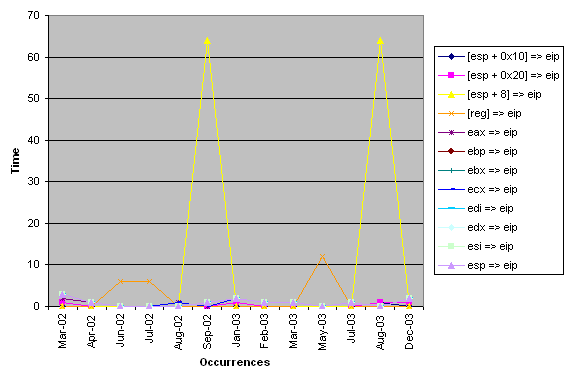
return address. Figure ![[*]](images/html/crossref.png) shows the spikes in more
detail. It's a shame that this technique was not published about
during those time frames! Never again in the lifetime of anyone who
reads this paper will there be such an occurrence.
shows the spikes in more
detail. It's a shame that this technique was not published about
during those time frames! Never again in the lifetime of anyone who
reads this paper will there be such an occurrence.
Perhaps of more interest than past occurrences of certain opcode
groups is what will come in the future. The table in figure
![[*]](images/html/crossref.png) shows the upcoming viable opcode windows for
2005.
shows the upcoming viable opcode windows for
2005.
| Date | Opcode Group |
|---|---|
| Sun Sep 25 22:08:50 CDT 2005 | eax => eip |
| Sun Sep 25 22:15:59 CDT 2005 | ecx => eip |
| Sun Sep 25 22:23:09 CDT 2005 | edx => eip |
| Sun Sep 25 22:30:18 CDT 2005 | ebx => eip |
| Sun Sep 25 22:37:28 CDT 2005 | esp => eip |
| Sun Sep 25 22:44:37 CDT 2005 | ebp => eip |
| Sun Sep 25 22:51:47 CDT 2005 | esi => eip |
| Sun Sep 25 22:58:56 CDT 2005 | edi => eip |
| Tue Sep 27 04:41:21 CDT 2005 | eax => eip |
| Tue Sep 27 04:48:30 CDT 2005 | ecx => eip |
| Tue Sep 27 04:55:40 CDT 2005 | edx => eip |
| Tue Sep 27 05:02:49 CDT 2005 | ebx => eip |
| Tue Sep 27 05:09:59 CDT 2005 | esp => eip |
| Tue Sep 27 05:17:08 CDT 2005 | ebp => eip |
| Tue Sep 27 05:24:18 CDT 2005 | esi => eip |
| Tue Sep 27 05:31:27 CDT 2005 | edi => eip |
| Tue Sep 27 06:43:02 CDT 2005 | [esp + 0x20] => eip |
| Fri Oct 14 14:36:48 CDT 2005 | eax => eip |
| Sat Oct 15 21:09:19 CDT 2005 | ecx => eip |
| Mon Oct 17 03:41:50 CDT 2005 | edx => eip |
| Tue Oct 18 10:14:22 CDT 2005 | ebx => eip |
| Wed Oct 19 16:46:53 CDT 2005 | esp => eip |
| Thu Oct 20 23:19:24 CDT 2005 | ebp => eip |
| Sat Oct 22 05:51:55 CDT 2005 | esi => eip |
| Sun Oct 23 12:24:26 CDT 2005 | edi => eip |
| Thu Nov 03 23:17:07 CST 2005 | eax => eip |
| Sat Nov 05 05:49:38 CST 2005 | ecx => eip |
| Sun Nov 06 12:22:09 CST 2005 | edx => eip |
| Mon Nov 07 18:54:40 CST 2005 | ebx => eip |
| Wed Nov 09 01:27:11 CST 2005 | esp => eip |
| Thu Nov 10 07:59:42 CST 2005 | ebp => eip |
| Fri Nov 11 14:32:14 CST 2005 | esi => eip |
| Sat Nov 12 21:04:45 CST 2005 | edi => eip |